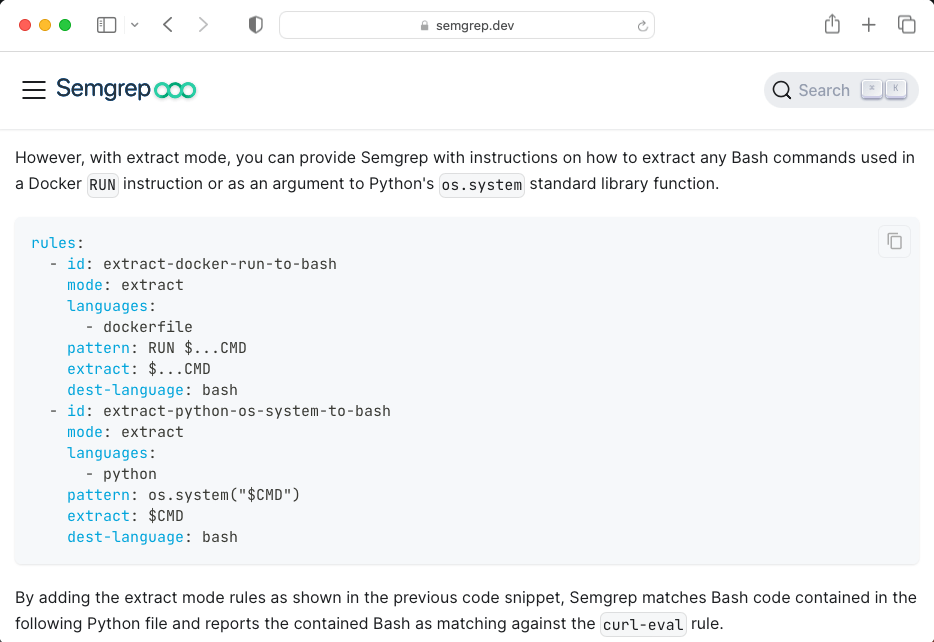
Now here’s two tools I wish I was more experienced with - Semgrep and Jupyter. Beyond this cool article from NCC, I’m interested to hear from anyone who uses either one of these tools. How did you get started, what do you do with them, etc…
You must log in or register to comment.
I used semgrep in the past, my team is still evaluating which tool for SAST to use as a standard internally but we are mostly oriented on CodeQL
What do you like about CodeQL? Haven’t used that yet either.
Report quality (less FP) compared to semgrep, snyk and sonarcloud but a killer feature for me is that you get the call paths so you can see when and how a vulnerable dependency is called. Pretty useful on big codebases.